When you analyze a malware, the first thing to do is static Analysis.
Things that could be useful, are:
- Fingerprint (or hashing): MD5, SHA256…
- unique fingerprint of a file / malware
- if we have two files written in a different way, but they do the same thing, even if they’re different for just 1bit, it will result in completely different hash
- Upload it on VirusTotal and find out if it has already been detected as malware
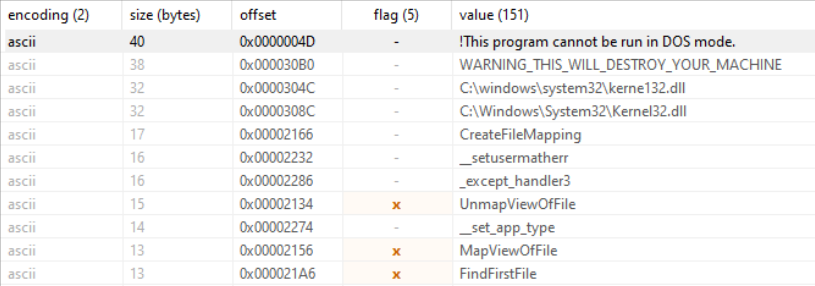
- Find strings
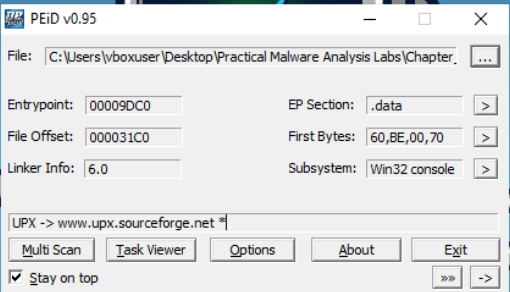
- Finding out if we have encountered a Packed malware
- Very often malware hides themselves, and a packer is used to hide the real program (exe), therefore we need to find out what in general have been used to pack the malware
- We can use PEiD, that will show if a malware is packed with a tool rather than another one, to understand more on its PE
- Analyze imports and libraries (we can use PEStudio or Dependency Walker)
- Common DLLs
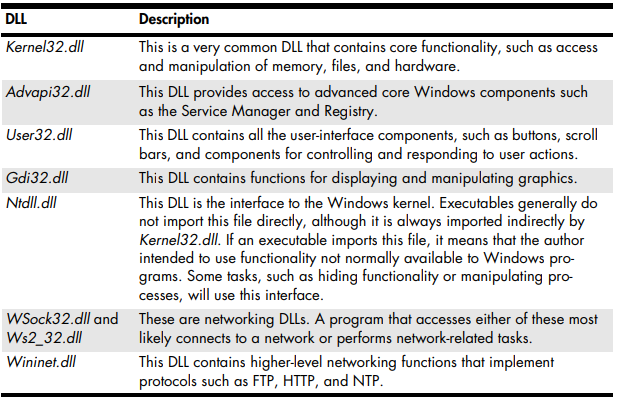
- Common DLLs
- We also need to analyze eventual manifest and resources files using PEStudio or Resource Hacker