Lab1-1
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
Questions
- Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
- DO IT LATER
- When were these files compiled?
- The exe
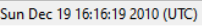
- The DLL
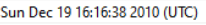
- The exe
- Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
- No, they’re not packed because PEiD shows “C++ Compiler”, and there is no sign of packing while reviewing PE in PEStudio
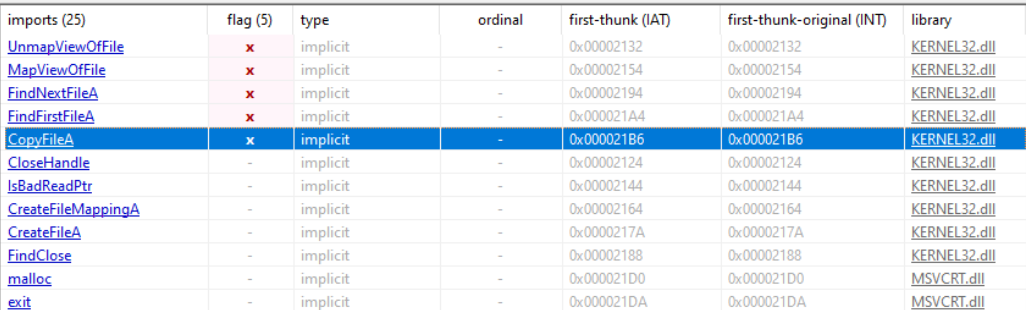
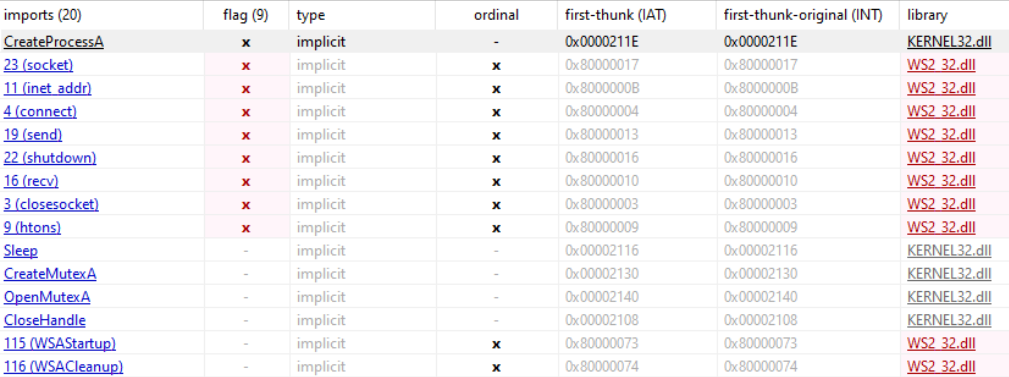
- Do any imports hint at what this malware does? If so, which imports are they?
- The executable, with these imports, it will probably look for a specific file or folder and copy itself
- The DLL listens for remote commands, because it implements a network socket
- The executable, with these imports, it will probably look for a specific file or folder and copy itself
- Are there any other files or host-based indicators that you could look for on infected systems?
- strings
- on DLL, there are interesting strings, like
CreateProcess(to probably invoke other processes) and127.26.152.13that could be a C2C IP Address - on EXE, CopyFile, FindFirstFile, FindNextFile, “WARNING THIS PROGRAM WILL DESTROY YOUR MACHINE”
- on DLL, there are interesting strings, like
- strings
- What network-based indicators could be used to find this malware on infected machines?
- No way for now
- IP ADDRESS
- No way for now
- What would you guess is the purpose of these files?
- EXE: executes DLL
- DLL: accept inputs from C2C command center
We’ve missed kerne132.dll from strings, because it was a subtle difference (typo)